This PSEB 10th Class Computer Notes Chapter 6 Operating Systems will help you in revision during exams.
PSEB 10th Class Computer Notes Chapter 6 Operating Systems
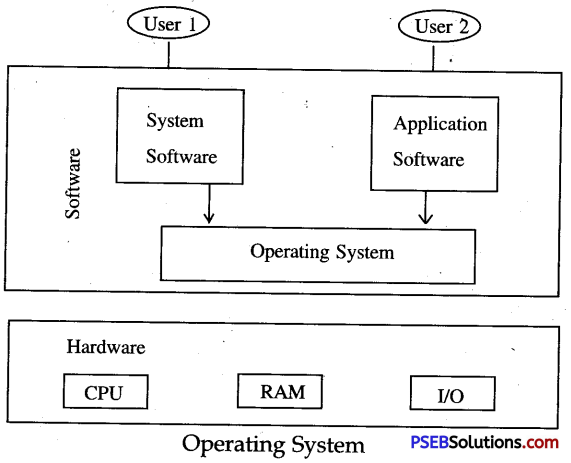
An operating system is an integrated collections of programs that acts as an interface between user program and computer hardware. It takes control over the operation of the computer to the extent of being able to allow a number of programs to be run on the computer without user intervention.
Operating system provides an environment in which a user may execute programs. The primary goal of an operating system is to make computer system convenient to use. It controls execution of processes and handles interrupts so that user can easily proceed.
Definitions of Operating System:
According to Rouse , “An operating system (OS) is the program that, after being initially Iqaded into the computer by a boot program, manages all the other programs in a computer.”
According to Computer Dictionary, “An operating system, or “OS,” is software that communicates with the hardware and allows other programs to run.” 1
According to Dictionary.com, “Operating system is the collection of software that directs a computer’s operations,controlling and scheduling the execution df other programs, andmanaging storage, input/output, and communication resources.”
Services Provided by Operating System
An Operating System provides services to both the users and to the programs.
- It provides programs an environment to execute.
- It provides users the services to execute the programs in a convenient manner.
Following are a few common services provided by an operating system :
Program Execution
Operating systems handle many kinds of activities from user programs to system programs like printer spooler, name servers, file server, etc. Each of these activities is encapsulated as a process.A process includes the complete execution context (code to execute, data to manipulate, registers, OS resources in use).
Following are the major activities of an operating system with respect to program management:
- Loads a program into memory.
- Executes the program.
- Handles program’s execution.
- Provides a mechanism for process synchronization.
- Provides a mechanism for process communication.
- Provides a mechanism for deadlock handling.
I/O Operation:
An I/O subsystem comprises of I/O devices and their corresponding driver software. Drivers hide the peculiarities of specific hardware devices from the users.
An Operating System manages the communication between user and device drivers. .
1. I/O operation means read or write operation with any file or any specific I/O device.
2. Operating system provides the access to the required I/O device when required.
File System Manipulation:
File manipulation refers to wide variety of operations which are available and allow us to delete ,copy, move. As we know a file represents a collection of related information. Computers can store files on the disk (secondary storage), for longterm storage purpose. Examples of storage media include magnetic tape, magnetic disk and optical disk drives like CD, DVD.
Each of these media has its own properties like speed, capacity, data transfer rate and data access methods. A file system is normally organized into directories for easy navigation and usage. These directories may contain files and other directions.
Following are the major activities of an operating system with respect to file management:
Program needs to read a file or write a file.
- The operating system gives the permission to the program for operation on file.
- Permission varies from read-only, read-write, denied and so on.
- Operating System provides an interface to the user to create/delete files.
- Operating System provides an interface to the user to create/ delete directories.
- Operating System provides an interface to create the backup of file system.
Communication:
In case of distributed systems which are a collection of processors that do not share memory, peripheral devices, or a clock, the operating system manages communications between all the processes. Multiple processes communicate with one another through communication lines in the network. The OS handles routing and connection strategies, and the problems of contention and security.
Following are the major activities of an operating system with respect to communication:
Two processes often require data to be transferred between them:
1. Both the processes can be on one computer or on different computers, but are connected through a computer network.
2. Communication may be implemented by two methods, either by Shared Memory or by Message Passing.
Error Detection:
Errors can occur anytime and anywhere. An error may occur in CPU, in I/O devices or in the memory hardware.
Following are the major activities of an operating system with respect to error detection:
1. The OS constantly checks for possible errors.
2. The OS takes an appropriate action to ensure correct and consistent computing.
Resource Management
In case of multi-user or multi-tasking environment, resources such as main memory, CPU cycles and files storage are to be allocated to each user or job.
Following are the major activities of an operating system with respect to resource management :
1. CPU scheduling algorithms are used for better utilization of CPU.
2. It acts like a resource manager. The OS manages all kinds of resources using schedulers.
Protection:
Considering a computer system having multiple users and concurrent execution of multiple processes, the various processes must be protected from each other’s activities.Protection refers to a mechanism or a way to control the access of programs, processes, or users to the resources defined by a computer system.
Following are the major activities of an operating system with respect to protection:
1. The OS ensures that all access to system resources is controlled.
2. The OS ensures that external I/O devices are protected from invalid access attempts.
3. The OS provides authentication features for each user by means of passwords.
Types of Operating Systems:
An operating system may be single user or multi user. There are mainly five types of operating systems:
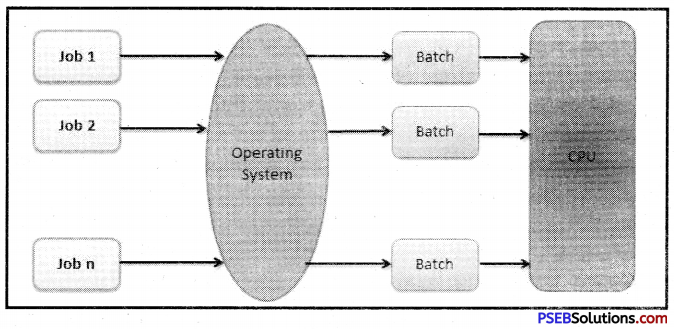
Batch Processing
Batch processing is one of the oldest method’s of running programs that are being used by many data processing centers for processing their jobs. It is based on the idea of automatic job-to-job transaction facility provided by almost all operating systems. In a batch mode, each user prepares his program off-line and submits it to the computer center.
A computer operator collects the program which have been punched on cards and stacks one program or job on top of another. When a batch of programs have been collected, the operator loads this batch of program into the computer. At one time they are executed one after another. Finally the operator retrieves the printed outputs of all these jobs and return them to the concerned users.
An operating system does the following activities related to batch processing:
1. The OS defines a job which has predefined sequence of commands, programs and data as a single unit.
2. The OS keeps a number a jobs in memory and executes them without any manual information.
3. Jobs are processed in the order of submission, i.e., first come first served fashion.
4. When a job completes its execution, its memory is released and the output for the job gets copied into an output spool for later printing or processing.
Advantages:
1. Batch processing takes much of the work of the operator to the computer.
2. Increased performance as a new job get started as soon as the previous job is finished, without any manual intervention.
Disadvantages:
- Difficult to debug program.
- A job could enter an infinite loop.
- Due to lack of protection scheme, one batch job can affect pending jobs.
Time-Sharing:
A real-time system is defined as a data processing system in which the time interval required to process and respond to inputs is so small that it controls the environment. The time taken by the system to respond to an input and display of required updated information is termed as the response time. So in this method, the response time is very less as compared to online processing.
Real-time systems are used when there are rigid time requirements on the operation of a processor or the flow of data. A real-time operating system must have well-defined, fixed time constraints, otherwise the system will fail.
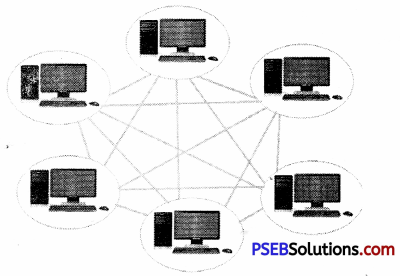
Distributed Operating System
Distributed systems use multiple central processors to serve multiple real-time applications and multiple users. Data processing jobs are distributed among the processors accordingly.The processors communicate with one another through various communication lines (such as high-speed buses or telephone lines). These are referred as loosely coupled systems or distributed systems. Processors in a distributed system may vary in size and function. These processors are referred as sites, nodes, computers, and so on. The advantages of distributed systems are as follows:
- With resource sharing facility, a user at one site may be able to use the resources available at another.
- Speedup the exchange of data with one another via electronic mail.
- If one site fails in a distributed system, the remaining sites can potentially continue operating.
- Better service to the customers.
- Reduction of the load on the host computer.
- Reduction of delays in data processing.
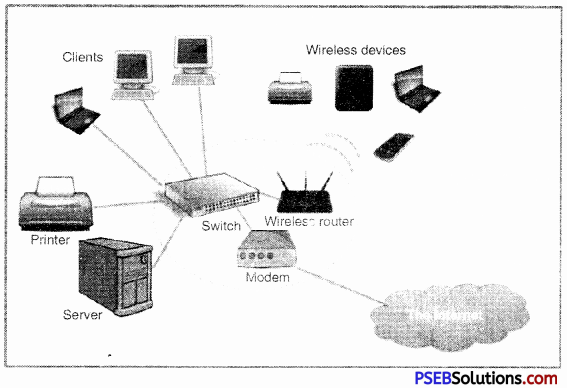
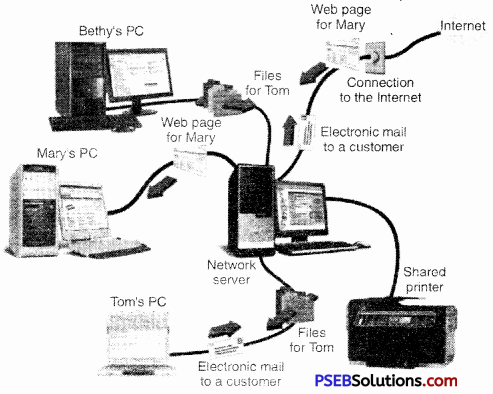
Network Operating System:
A Network Operating System runs on a server arid provides the server the capability to manage data, users, groups, security, applications, and other networking functions. The primary purpose of the network operating system is to allow shared file and printer access among multiple computers in a network, typically a local area network (LAN), a private network or to other networks.
Examples of network operating systems include Microsoft Windows Server 2003, Microsoft Windows Server 2008, UNIX, Linux, Mac OS X, Novell NetWare and BSD.
The advantages of network operating systems are as follows:
- Centralized servers are highly stable.
- Security is server-managed.
- Upgrades to new technologies and hardware can be easily integrated into the system.
- Remote access to servers is possible from different locations and types of systems.
The disadvantages of network operating systems are as follows:
- High cost of buying and running a server.
- Dependency on a central location(server) for most operations.
- Regular maintenance and updates are required.
Multi Programming. Multi Programming Operating System is the name given to the interleaved execution of two or more different and independent programs by the same computer. Interleaving of programs mean chain of programs that are either in running phase, ready or blocked phase. It is an efficient way to improve the system performance.
Multi programming approach permits more than one job to utilize the CPU time at any moment by applying the scheduling techniques like first come first serve, shortest job first etc . The more the number of programs requesting for system resources, resource utilization would be better. The operating system picks up any of the programs as scheduled and starts execution.
An OS does the following activities related to multiprogramming.
- The operating system keeps several jobs in memory at a time, This set of jobs is a subset of the jobs kept in the job pool.
- The operating system picks and begins to execute one of the jobs in the memory.
- Multiprogramming operating systems monitor the state of all active programs and system resources using memory management programs to ensure that the CPU is never idle, unless there are no jobs to process.
Advantages:
High and efficient CPU utilization.
User feels that many programs are allotted CPU almost simultaneously.
Disadvantages:
CPU scheduling is required.
To accommodate many jobs in memory, memory management is required.
Real-Time Processing:
It is a form of operating system that are used in environments where a large number of events mostly external to computer systems,- must be accomplished and proceed in a short time or within certain deadline. Processing method is one that controls the environment by receiving the data, processing them and taking action or returning results sufficiently quickly to affect the functioning of the environment at that time. The term real time refers to the technique of updating files with the transaction data immediately after the event that it relates. It is quite different from batch processing that processors related data in batches at predefined periods of time.
Real time systems are basically on-line systems with one specialty in inquiry processing. The response of the system to the inquiry itself is used to control the activity. An on line production data collection system that simply accepts input and utilizes it for payroll and costing purposes cannot be terminated as real time but on the other hand, the system is designed to provide immediate information to monitor the production processes.
Differences Between Dos and Windows:
The differences between DOS and Windows are as follows:
| DOS |
Windows |
| 1. It is single User operating system |
1. It is multi User operating system |
| 2. It is single-tasking operating system |
2. It is Multi-tasking operating system |
| 3. It does not time-sharing |
3. It uses time-sharing |
| 4. Keyboard is main input device |
4. Keyboard and Mouse are mainly used. |
| 5. It is character user interface |
5. It is graphical user interface |
| 6. It is light software. |
6. It is heavy software |
| 7. It doesn’t support multimedia |
7. It supports multimedia. |
| 8. It is mainly used to manage files |
8. It is used for many purposes. |
| 9. It can be stored on floppy disk |
9. It cannot be stored on floppy disk. |
| 10. Its production is slopped. |
10. It is still developed by Microsoft. |
| 11. It can connect to internet |
11. It cannot connect to internet |
| 12. It cannot use mouse |
12. It can use mouse for input. |
LINUX:
Just like Windows XP, Windows 7, Windows 8, and Mac OS X, Linux is an operating system. An operating system is software that manages all of the hardware resources associated with your desktop or laptop. To put it simply – the operating system manages the communication between your software and your hardware. Without the operating system (often referred to as the “OS”), the software wouldn’t function.
Linux is one of popular version of UNIX operating System. It is open source as its source code is freely available. It is free to use. Linux was designed considering UNIX compatibility. Its functionality list is quite similar to that of UNIX.
Basic Features
Following are some of the important features of Linux Operating System:
- Portable: Portability means softwares can works on different types of hardwares in same way. Linux kernel and application programs supports their installation on any kind of hardware platform,
- Open Source: Linux source code is freely available and it is community based development project. Multiple teams works in collaboration to enhance the capability of Linux operating system and it is continuously evolving.
- Multi-User: Linux is a multiuser system means multiple users can access system resources like memory/ ram/ application programs at same time.
- Multi Programming: Linux is a multiprogramming system means multiple applications can run at same time.
- Hierarchical File System: Linux provides a standard file structure in which system files/ user files are arranged.
- Shell: Linux provides a special interpreter program which can be used to execute commands of the operating system. It can be used to do various types of operations, call application programs etc.
- Security: Linux provides user security using authentication features like password protection/ controlled access to specific files/ encryption of data. Components of Linux System
Linux Operating System has primarily three components
- Kernel: KemeHs the core part of Linux. It is responsible for all major activities of this operating system. It consists of various modules and it interacts directly with the underlying hardware. Kernel provides the required abstraction to hide low level hardware details to system gr application programs.
- System Library: System libraries are special functions or programs using which application programs or system utilities accesses Kernel’s features. These libraries implement most of the functionalities of the operating’system and do not requires kernel module’s code access rights.
- System Utility: System utility programs are responsible to do specialized, individual-level tasks.
Computer Security:
Computer Security is the process of detecting and preventing any unauthorized use of your laptop/computer. It involves the process of safeguarding against trespassers from i jing your personal or office based computer resources with malicious intent or for their own gains, or even for gaining any access to them accidentally.
Install Antivirus Protection:
Antivirus and anti-malware software are essentials in your arsenal of online security weapons as well.
Anti Spyware Software:
Spyware are different from viruses. Because they do not destroy our hardware or software. They get installed in the system and send senstive information like passwords, credit card information etc. to server. We need latest Anti spyware software to identify and remove spywares.
Use Strong Passwords:
Strong passwords are vital to good online security. Make your password difficult to guess by:
- using a combination of capital and lower-case letters, numbers and symbols
- making it between eight and 12 characters long
- avoiding the use of personal data
- changing it regularly
- never using it for multiple accounts
- using two-factor authentication.
Create a password policy for your business to help staff follow security best practice. Look into different technology solutions to enforce your password policy, e.g., scheduled password reset.
Update Programs and Systems Regularly:
Updates contain vital security upgrades that help protect against known bugs and vulnerabilities. Make sure that you keep your software and devices up-to-date to avoid falling prey to criminals.
Put Up a Firewall:
Firewalls are effectively gatekeepers between your computer and the internet, and one of the major barriers to cyber threats such as viruses and malware. Make sure that you set up your firewall devices properly; otherwise they may not be fully effective.

![]()





![]()

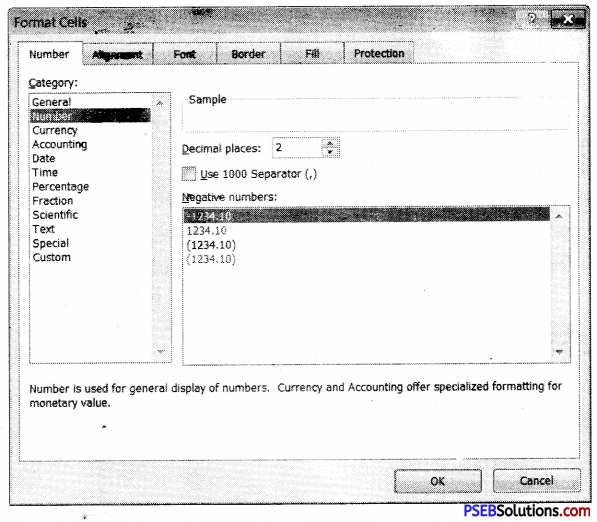
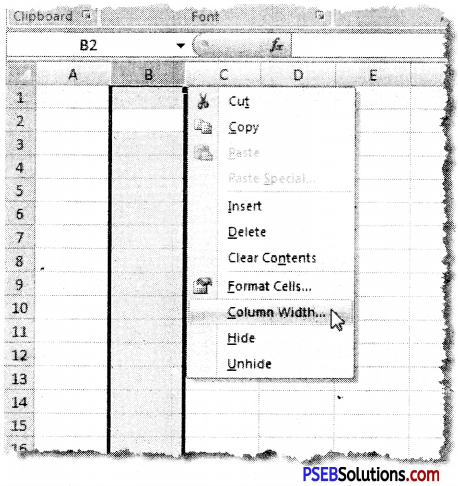
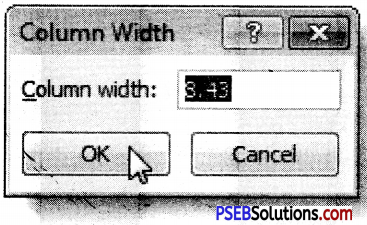
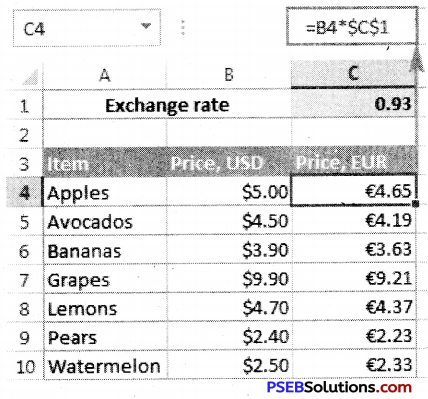
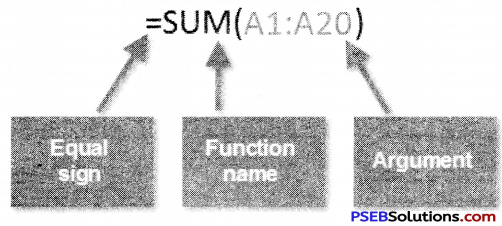
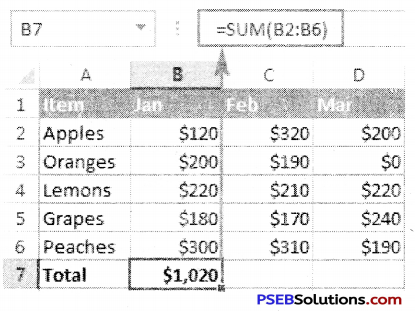
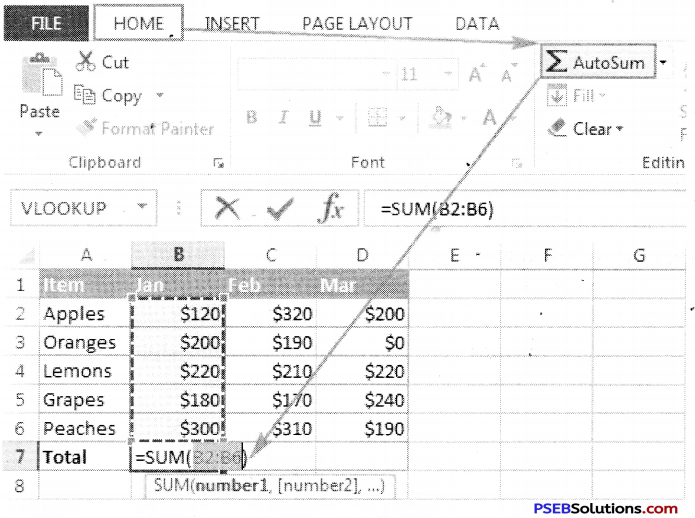
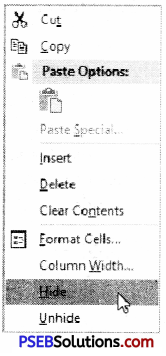
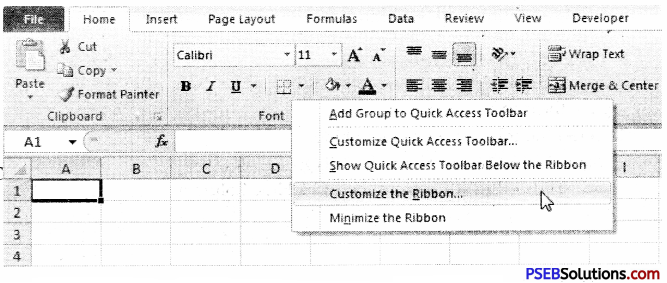
 The “Format Cells” window can be opened in from the right-click menu. Formatting options are available on the Home Tab on the Font, Alignment, and Number groups.
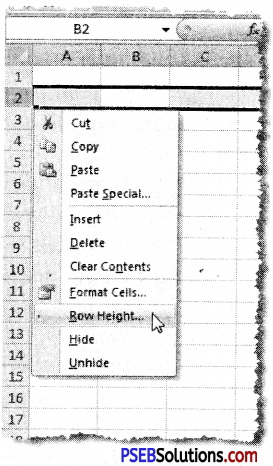
The “Format Cells” window can be opened in from the right-click menu. Formatting options are available on the Home Tab on the Font, Alignment, and Number groups.